Table of Content
The finest free online vulnerability scanners are these like Sucuri, Quterra, and AsafaWeb. They are simple to function with out sacrificing an excessive amount of in detailed reporting. Nmap is a traditional open-source tool used by many network admins for primary handbook vulnerability administration. This free vulnerability scanner principally sends packets and reads responses to discover hosts and providers throughout the community.
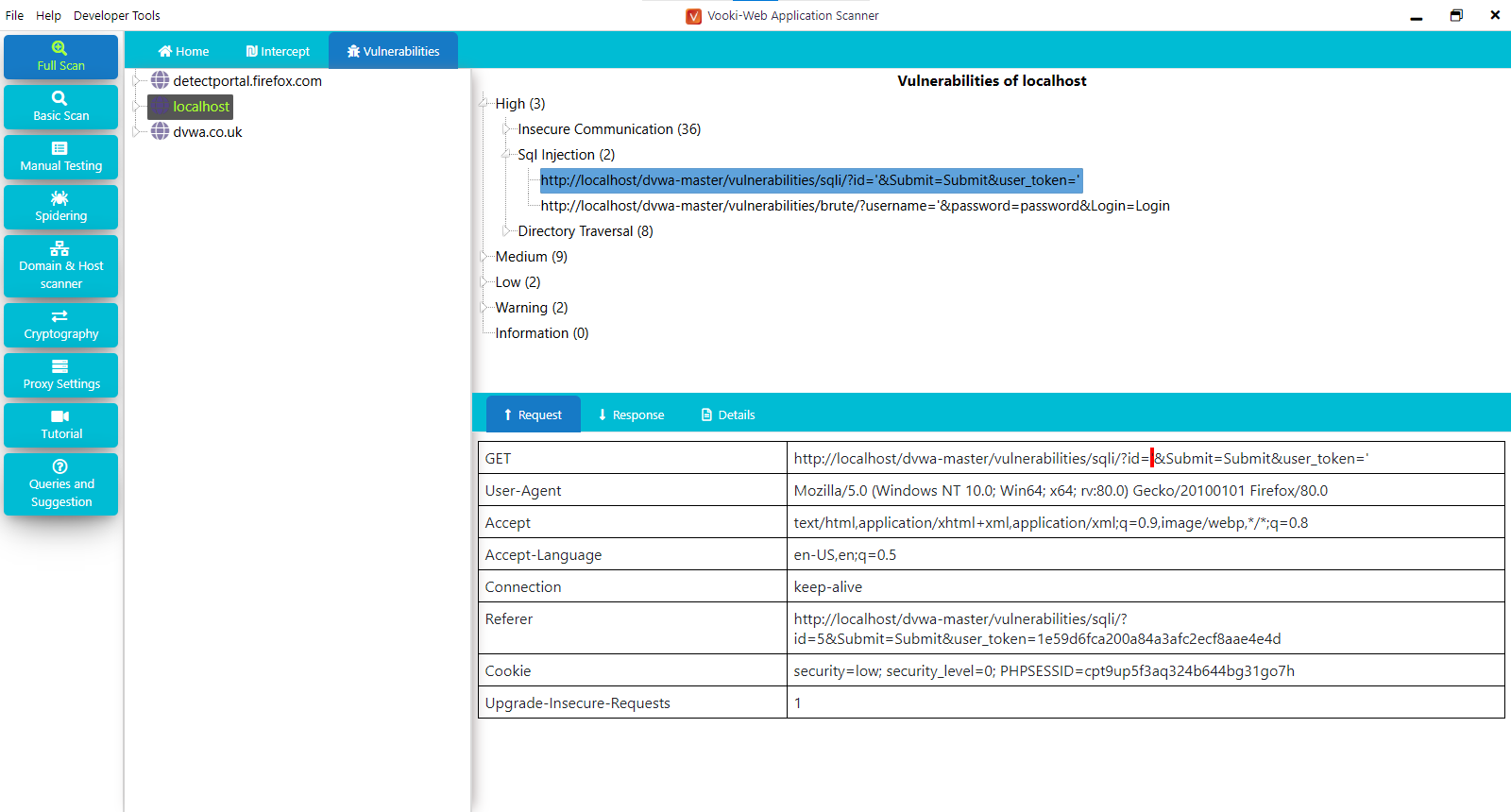
Attackers typically present a malicious hyperlink to a person and urge them to click on on it to start out an XSS attack. We consider that Acunetix is the best vulnerability scanner as a end result of it is the most automated, the most efficient, and probably the most correct scanner on the market. If you want to find out for yourself, check it together with other scanners. A vulnerability scanner sends special data to your web site or net utility – the type of data that a malicious hacker would send. If the response out of your web site or net software reveals that it can be hacked, the vulnerability scanner reviews it to you and tells you the means to repair it. One of the popular website security scanners, ImmuniWeb, checks your web site against the following standards.
Sorted By Danger Rating
This well-known open-source community protocol analyzer helps with sure vulnerability scanning tasks. The Wireshark free vulnerability scanner depends on packet sniffing to grasp network visitors, which helps admins design efficient countermeasures. If it detects worrisome visitors, it can assist to find out whether or not it’s an assault or error, categorize the attack, and even implement rules to guard the community.
Vulnerabilities with commonplace signatures, such as cross-site scripting , may be reliably found. Some path traversal vulnerabilities may be detected by submitting a traversal sequence targeting a identified file, and searching the response for the looks of this file. Simulating actual world safety events, testing vulnerabilities and incident response.
Better Vulnerability DiscoveryFaster Pentest Reporting
Essentially, it enables you to ensure your security measures are effective by subjecting them to common testing and validation. Because of the tools’ emphasis on accuracy, they may end in exposures of delicate information, as nicely as impacts on efficiency. Helps firms cut back their cybersecurity risk by detecting information exposures and controlling third-party danger. It uses security rankings and steady information leak detection to stop security breaches. Users say UpGuard is simple to implement, helps monitor workflows, control surface safety, and prioritize risks for straightforward and efficient remediation. UpGuard makes use of a mix of third-party safety scores, vendor questionnaires, and risk intelligence scanning to help organizations reduce their danger.
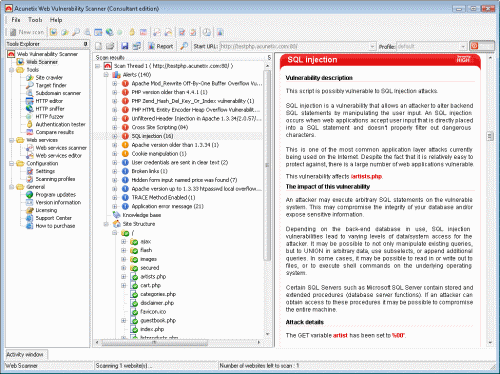
These sorts of public-facing property are common assault vectors for malicious actors seeking unauthorized access to methods and data. Vulnerability scanning helps to minimize threat and management vulnerabilities from the very starting of website improvement. PortSwigger's application safety testing products each use the same underlying web vulnerability scanner - Burp Scanner. Whether you need software program designed for an individual tester trying to enhance workflows, or enterprises eager to scale and automate, there's a Burp Suite for everyone. AppScan has several versions for the enterprise, the cloud, and more. AppScan on Cloud, for instance, is a cloud-based application security resolution that provides AppScan as a service.
Add Target
One advantage of Qualys Community Edition is the flexibility to search by way of scan results and create flexible reports. This tool supplies thorough infrastructure monitoring, permitting admins to take inventory of the community, applications, servers, and more. The platform can monitor status adjustments to units and alert you to any important changes, as the bizarre activity may indicate an intrusion. It can use packet sniffing to scan SNMP entice information and port exercise, too. Breach and assault simulation – This is much like pen testing but is ongoing, automated, and quantifiable.
However, if you need to scan often, you might want to leverage an open-source vulnerabilities scanner or SaaS-based. Fully supported by ethical hackers, the Detectify domain and net application security service offer automated safety and asset monitoring to detect greater than 1500 vulnerabilities. Even if end customers can at present entry their files and your community connectivity appears fantastic, you can’t assume the security of your network. Every network has some security gap that bad actors or malware may exploit.
Website Scanner Velocity Improvements
To avoid vulnerabilities, look ahead to firewall or OS misconfigurations. Addressing issues – Once you’ve recognized priority dangers, addressing them could be a daunting task. The proper software may help you automate the process of provisioning gadgets.
This free, cloud-based service replaces the older Qualys FreeScan tool. Community Edition offers a pared-down model of the Qualys Cloud Platform acceptable for small organizations, because it provides unlimited scanning for 16 inner property, three external belongings, and one URL. It comes with lots of the features of the complete tool, as the platform attracts on info from over three billion yearly vulnerability scans.
Power Your Corporation
The BeyondTrust Retina software can scan across your network, web providers, containers, databases, virtual environments, and even IoT units. Its built-in IoT compatibility and audits aren’t found in all scanner tools on the market, so this could be a great possibility if you need to manage an array of gadgets. At the identical time, it’s designed to scan without affecting availability or efficiency. This program compares threats to a vulnerability database somewhat than relying on anomaly detection. Countermeasure implementation – Not all safety tools each establish points and give admins a way to automatically handle them. Some VM tools are centered on monitoring completely, leaving it up to admins to take the next step.
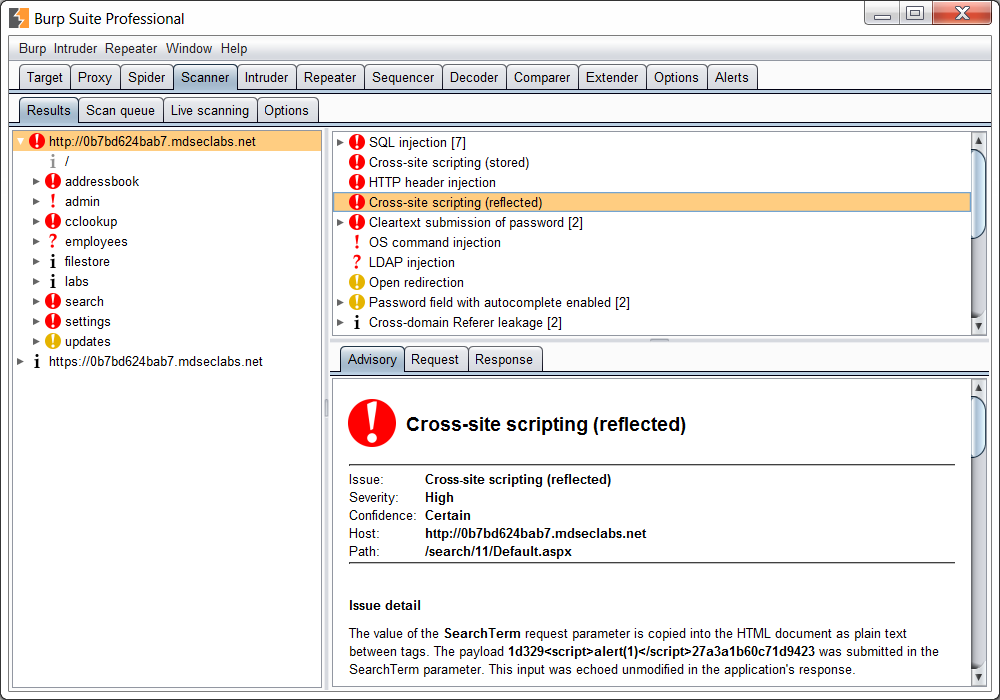
WAVSEP is totally unrelated to OWASP and we don't endorse its results, nor any of the DAST tools it evaluates. However, the results supplied by WAVSEP may be useful to somebody excited about researching or selecting free and/or industrial DAST tools for their projects. This project has way more detail on DAST tools and their features than this OWASP DAST page. Digging deeper, our various web CMS scanners allow you to uncover Wordpress, Drupal, Joomla, and SharePoint vulnerabilities. And you presumably can additional discover all of these with the URL Fuzzer and Password Auditor instruments. You can use the Subdomains Finder and the dedicated instruments to Find Virtual Hosts for every internet utility.


No comments:
Post a Comment